
One App For All Team Communication Needs
Gem Team brings everyday communication and operations into a single, secure workspace. Teams chat, call, share files, and co-edit in real time without switching tools. The interface feels instantly familiar to people used to WhatsApp or Telegram, yet it adds the structure enterprises expect. For leaders, the value is simple: faster decisions in one place; for IT and security, transparent control over data and compliance.
Table of Contents
The Problem Gem Soft Set Out To Solve
Enterprises have been forced to stitch together fragmented, cloud-only platforms that aren’t built for strict data governance. Each extra tool multiplies risk, enlarges the attack surface, and complicates compliance. Gem Team replaces this patchwork with a unified, security-first platform that handles messaging, collaboration, and task flow under consistent policies and auditability.
Unified Communication Without The Tool Sprawl
Conversations flow seamlessly across text, voice, and video, while files and threads remain organized. Video meetings scale to 300 participants, featuring screen sharing, recording, and moderator controls, making it practical for all-hands meetings, partner briefings, and incident bridges. Smart messaging features such as presence, message editing, and delivery confirmations keep discussions clear and actionable. History and file storage are not artificially capped, so teams don’t lose context when projects run long.
Security First By Design, Not as An Afterthought
Gem Team minimizes data exposure and only accesses what is needed to provide the service. Metadata is anonymized or avoided where possible. Transport is protected with TLS 1.3, messages and metadata are encrypted, and storage is encrypted at rest. The platform is built for mission-critical continuity on fail-safe cluster servers with robust backup concepts. Hosting partners meet Uptime Institute Tier III facility and management certifications, which help keep communication available when it matters most.
Data sovereignty is a default principle. Customers decide where information is stored, who can access it, how long it persists, and when it is automatically removed from servers and end devices. Policies map cleanly to ISO, GDPR, and GCC requirements, including Qatar’s CRA, so regional governance rules are easier to meet in practice rather than only on paper.
Architecture That Fits Your Compliance Posture
Every organization can choose between on-premise deployment and secure cloud hosting. Many blend both to match sensitivity levels across departments. Optional IP masking and metadata shredding reduce residual traceability. Fine-grained access controls and complete audit trails support separation of duties, least privilege, and investigatory needs. For restricted environments, air-gapped deployment keeps critical networks isolated without losing day-to-day usability.
How Gem Team Compares With Slack, Microsoft Teams, and Google Chat
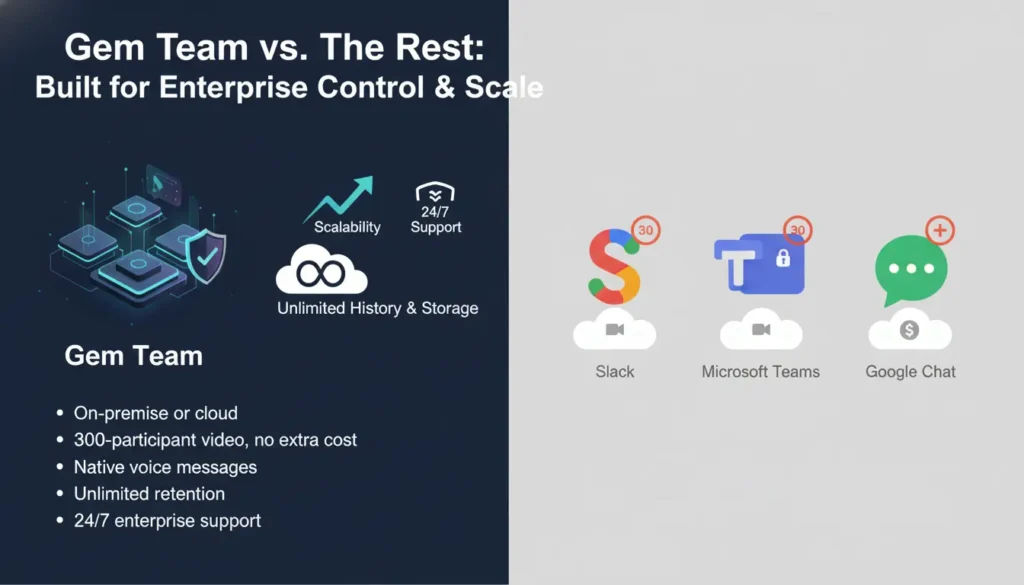
Gem Team focuses on control, scale, and custom fit. It offers on-premise or cloud deployment, while the major incumbents are primarily cloud only. Video meetings support up to 300 participants out of the box and include recording without bolt-on fees. Voice messages are supported natively. Organizational profiles are first-class, not just contact lists. Message history and file storage are effectively unlimited, removing the surprise of retention ceilings during audits. Support is available 24/7, depending on the package, so enterprises are not left to self-serve during incidents. For many regulated or high-sensitivity operations, these differences are decisive.
Where Gem Team Makes The Biggest Difference
Companies with field, on-site, or mobile staff benefit from a messenger that feels intuitive and still meets corporate guardrails. When cloud outages or cyber events occur, a fail-safe channel preserves command and control so operations can continue. Emergency and crisis teams can add alerting and geolocation to coordinate responses without switching systems. For C-level, R&D, and legal communications, multi-layer encryption and strict policies reduce the risk associated with sensitive discussions. And for organizations that require national data residency or sector mandates, Gem Team’s hosting models provide genuine sovereignty rather than promises.
Built With SSDLC And Transparent Security Practices
Security is embedded throughout the Secure Software Development Lifecycle. During development, the codebase is continuously checked with SAST and DAST, dependency and secret scanners. Before releases, the platform undergoes penetration testing and targeted checks for broken access control and IDOR issues. Repository and CI access are tightly governed, CI/CD pipelines are locked down, and infrastructure as code follows secure defaults. Audit logs, change tracking, and regular internal architecture reviews make the process traceable. The product team maintains a comprehensive security policy and secure coding guidelines and is prepared for certifications such as ISO 27001.
Enterprise AI Expertise On Your Terms
Gem’s team brings applied AI experience that respects security boundaries. Organizations can deploy LLM and ML workloads on-prem or in the cloud and tune inference performance for real-time responsiveness. Assistants can be embedded directly into chat to retrieve context, automate repetitive actions, and surface answers from internal knowledge. For broader needs, standalone assistants and RAG pipelines connect to documents and data in many formats. Multi-agent systems handle complex, hierarchical workflows. Fine-tuning, prompt design, dataset curation, and model evaluation are all aligned with governance requirements, and Gem can deliver end-to-end AI products that integrate cleanly with the secure messaging backbone.
Getting Started Without Disruption
Most teams begin by defining data residency, retention, and access control policies, then select on-premise, cloud, or a hybrid deployment. A pilot group validates integrations and migration paths, after which the rollout extends department by department. Because users encounter a familiar chat and call experience, training time is short and adoption is steady. From there, security teams can tighten policies as needed and extend the platform with customizations that reflect internal processes.
Frequently Asked Questions
Can the Gem Team run in a closed environment with no internet?
Yes. Air-gapped deployments are supported alongside standard on-premise setups.
How many people can join a single video conference?
Up to 300 participants, with screen sharing, recording, and moderator controls.
What does “data sovereignty” look like in practice?
You choose a hosting location and model, set retention and deletion policies, and can automatically remove data from servers and end devices after defined periods. All content and storage are encrypted, with TLS 1.3 securing transport.
How does Gem Team handle compliance across regions like the GCC or EU?
The platform’s SSDLC process, logging, access control, and encryption align with ISO and GDPR principles and can be adapted to country-specific rules, including Qatar’s CRA.
Is support truly available around the clock?
Yes. Packages include access to 24/7 support, so critical issues are not left until the morning.
Gem Team unifies communication and collaboration in one secure place, gives organizations real control over their data, and offers deployment flexibility that cloud-only services can’t match. For enterprises that need reliability, resilience, and privacy without sacrificing usability, it is a practical alternative to Slack and Microsoft Teams.